WELCOME TO BUMBLY BEE
Bumblybee.net is an website that gives the latest information on different topic
If you would like to purchase me and my friends go to www.mypillowpets.com
If you like to wear me on your feet go to Bunnyslippers.com
To learn the truth about God's word, visit faithdome.org - To watch a live Sunday Service that starts at 10:30 AM PST, or bible Study - click on YouTube.com in the "search bar" type "ever increasing faith" and then 5 minutes before click on the "EIFM" button.
For Cyber Information go to: paloaltonetwork.com/CyberACES
Toys that can spy on kids are called a growing concern - Click Here
Learn tactics NJ utility scammers use and how you can avoid them - Click Here
New tools to help NJ home-buyers assess flood risk - Click Here - flooddisclosure.nj.gov
Deer face hazards not just on roads, but in backyards - Click Here
FAFSA delay complicates college entry - Click Here
Baby lounger sold on Amazon deemed unsafe - Click Here
Mysterious dog illness hits East Coast, but not NJ - yet - Click Here
Bumbly Bee wants to reminds users that any link to another website is tested first.
A Bee note: For the latest information, that has to do with New Jersey, on the left side of the Home page, click on "Passaic County" or Wayne Township NJ" to see the latest information.
A Bee Reminder:
..... It is very important that you take your Key Bobs inside your house. It is also important that you lock your cars even in your own driveways. Also it is important that you turn off your cars when getting gas or running into the store. This will cut down on your vehicles from getting stolen!!
Bumbly bee note: This items listed below that do not have who it was printed by, comes from either New Jersey Cybersecurity & Communications Integration Cell Weekly Bulletin or from Life Lock.
CDC says eye drops linked to infections:
By: Mike Stobbe
Associated Press
NEW YORK - U. S. health officials are advising people to stop using over-the-counter eye drops that have been linked to an outbreak of drug-resistant infections.
..... The Centers for Disease Control and Prevention on Wednesday [02/01/2023] night sent a health alert to physicians, saying the outbreak includes at least 55 people in 12 states, one died.
..... Disease investigators have linked the infection, including some found in blood, urine and lungs, to EzriCare Artificial Tears. Many of the patients said they had used the product, which is a lubricant used to treat irritation and dryness.
..... The infections were all caused by a bacteria called Pseudomonas aeruginosa. Investigators detected that kind of bacteria in open EzriCare bottles, but further testing was underway to see if the strains matched.
..... EzriCare said it is not aware of any evidence definitively linking the outbreak to the product, but that it has stopped distributing the eye drops. It also has a notice on its website urging consumers to stop using the drops.
LG to invest $4.5 billion in US battery operation:
..... LG Energy Solution will invest more than $4.5 billion in U.S. battery production by 2025 as more automakers commit to churning out electric vehicles sooner than anyone had expected.
..... The Korean company, which has a joint venture with U.S. automaker General Motors, said the investment will help crate 10,000 jobs, including subcontractors.
..... GM and LG are currently building a $2.3 billion battery factory in Lordstown Ohio, near Cleveland, that will employ about 1,000 people when it is completed in 2022.
..... General Motors has vowed to make its entire global fleet largely electric by 2035, even changing its corporate logo to include the likeness of an electric plug.
|
|
|
|
|
|
|
Image Source: Inky |
|
US opens probe of steering problems in Honda sedans:
..... The U.S. government's auto safety agency is investigating multiple complaints about steering failures that could affect more than 1.1 million Honda Accord sedans.
..... In documents posted Monday, [05/10/2021] the National Highway Traffic Safety Administration says it received 31 complaints about the problem, and Honda has 77 more. Owners complained about a loss of steering control and the cares veering from their intended travel path. Two crashes and two injuries were reported.
..... The probe covers Accords from the 2013 through 2015 model years. The agency opened the probe after getting a petition from an owner in October of last year. [2020] It will investigate how often the problem happens., how many vehicles are affected, and the safety consequences of the problem. The probem could lead to a recall.
|
|
|
|
|
|
|
New Ford models can get software updates via Internet:
..... Ford says it is starting to send out over-the-Internet software updates to some of its newer models as it match electric car maker Tesla.
.....At present the updates are only available to about 100,000 owners of 2021 model year F-150s, Mustang Mach-Es and the upcoming Bronco, but Ford plans to spread the tech across its entire lineup as models are updated. It plans to make 33 million vehicles with the capability by 2028.
..... The updates can fix software glitches in nearly all of the vehicles' computers, and will be able to make recall repairs, offer new features and cut warranty claims, said Alex Purdy, the company's connectivity business director.
..... Ford says there are about 80 different computers in its most sophisticated vehicles that control everything from the infotainment center to breaks and transmission shifts.
Supreme Court: Mortgage overseer structure unconstitutional:
..... The Supreme Court on Wednesday [06/23/2021] gave the president greater power to fire the head of the agency that oversees mortgage giants Fannie Mae and Freddie Mac, ruling that the agency's structure violates the separation of powers principles in the Constitution.
..... Writing for a majority of the court, Justice Samuel Alito said that as the justices explained in a case last year, [2020] "the Constitution prohibits even 'modest restrictions; on the President's power to remove the head of an agency with a single top officer."
.... The ruling paves the way for President Joe Biden to remove Mark Calabria, who was nominated to head the Federal Housing Finance Agency in 2019 by then-President Donald Trump.
Judge dismisses antitrust lawsuits against Facebook:
..... A federal judge on Monday [06/28/2021] dismissed antitrust lawsuits brought against Facebook by the Federal Trade Commission and a coalition of state attorneys general, dealing a significant blow to attempts by regulators to rein in tech giants.
.... U.S. District Judge James Boasberg ruled Monday [06/28/2021] that the lawsuits were "legally insufficient" and didn't provide enough evidence to prove that Facebook was a monopoly. The ruling dismisses the complaint but not the case meaning the FTC could refile another complaint.
.... "These allegations - which do not even provide an estimated actual figure or range for Facebook's market share at any point over the past ten years - ultimately fall short of plausibly establishing that Facebook holds market power,: he said.
..... The U.S. government and 48 states and districts sued Facebook in December 2020, accusing the tech giant of abusing its market power in social networking to crush smaller competitors and seeking remedies that could include a forced spin-off of the social network's Instagram and WahtsApp messaging services.
High court won't hear florist's case:
Associated Press
WASHINGTON - the Supreme Court on Friday [07/02/2021] declined to take up the case of a florist who refused to provide services for a same-sex wedding, leaving in place a decision that she broke sate anti-discriminations laws.
..... Justice Clarence Thomas, Samuel Alito and Neil Gorsuch said they would have agreed to hear the case and review the decision. Four Justices are needed for the court to take a case..
..... In 2018 the high court ordered Washington sate court to take a new look at the case involving florist Barronelle Stutzman and her Arlene;s Flowers business. That followed the justices; decision in a different case involving a Colorado baker who declined to make a cake for a same-sex wedding.
.... After that review, the Washington Supreme Court ruled that state courts did not act with animosity toward religion when they ruled Stutzman broke the state's anti-discrimination laws by refusing to provide flowers for the wedding of Rob Ingersoli and Curt Freed.
China's Xi attacks calls for technology blockages:
..... Chinese leader Xi Jimping on Tuesday [07/06/2021] attacked calls from some in the U.S. and its allies to limit their dependency on Chinese suppliers and block the sharing of technologies.
..... In a speech to representatives of leftist political parties in more than 100 countries, Xi said China's ruling Communist Party has succeeded in raising the country from poverty and created a new model of development.
..... Such experiences should be shared and no country should :obstruct the development of other countries and harm their people's lives through political manipulation," Xi said.
..... Decoupling has become a byword from some in the U.S. and elsewhere for ending dependency on Chinese supply lines, especially for high-tech products such as smartphones and computers.
China criticizes us moves to expand financial sanctions:
BEIJING - China's government on Friday [07/09/2021] criticized new U.S. moves to reduce access to American financial markets and said it will protect Chinese companies but gave no indication of possible retaliation.
..... The S&P Dow Jones Indices and FTSE Russell removed more Chinese companies from their indexes after President Joe Biden expanded a blacklist of companies that are off limits to American investors. Such indexes are the basis for billions of dollars of investment in stocks and bonds.
..... A foreign ministry spokesman, Wang Wenbin, accused Washington of "abusing national power and generalizing the concept of national security to support Chinese enterprises for no reason."
Ford, Argo Al to deploy autonomous vehicle on Lyft network:
..... For motor Company and a self-driving vehicle company it partly owns will join with the Lyft rid-hailing service to offer autonomous rides on the Lyft network.
..... The service suing Ford vehicles and a driving system developed by Pittsburgh-based Argo Al will begin in Miami later this year [2021] and start in Austin, Texas, in 2022. It will stat with human backup drivers and go fully autonomous at an unspecified date.
..... The cars will gather data to lay the groundwork to deploy 1,000 robotaxis on the Lyft network in multiple markets during the next five years, the companies said Wednesday [07/21/2021] in a statement.
US looking into whether Ford was slow to recall cameras:
..... U.S. highway safety regulators are investigating whether Ford acted quickly enough when it recalled more than 620,000 vehicles last year [2020] to fix faulty rear-view cameras.
..... The National Highway Traffic Safety Administration also says it will look into whether the automaker should have recalled more vehicles.
..... documents posted Friday [08/06/2021] on the agency's website say Ford began the recall on September 23 [2020] because the backup camera displays can show a blank or distorted image.
..... The recall covered multiple Ford and Lincoln models form 2020 including the F-Series pickup, the nation's top-selling vehicle.
US probing whether Mercedes vans can roll away unexpectedly:
..... The U.S. government's highway safety agency is investigating whether some Mercedes-Benz Sprinter vans can shift out of park and unexpectedly roll away.
..... The problem by the National Highway Traffic Safety Administration covers an unknown number of vans from the 2019 model year. The agency says it has 11 complaints about the problem including eight crashes and one injury.
..... Some of the complaints say the gearshift indicator shows that the vans are in park, but they were able to roll away. One hit a house in Salt Lake City in September of 2020.
Peloton acknowledges subpoenas, SEC investigation:
..... Peloton has been subpoenaed by the Justice Department and the Department of Homeland security for documents and other information related to its reporting of injuries associated with its exercise equipment.
..... The company also said Friday [08/27/2021] that the Securities and exchange Commission is "investigating our public disclosures concerning these matters."
..... In May, [2021] Peloton recalled about 125,000 of its treadmills less than a month after denying they were dangerous despite the death of at least one child and injuries to 29 users.
..... The U.S. Consumer Product Safety Commission warned on April 17 [2021] that people with children and pets should immediately stop using the Tread+.
Unvaccinated face far more risk
By: Lauran Neergaard
Associated Press
..... New U.S. studies released Friday [09/10/2021] show the COVID-19 vaccines remained highly effective against hospitalizations and death even as the delta variant swept the country.
..... One study tracked over 600,000 COVID-19 cases in 13 states from April through mid-July. [2021]
..... As delta surged in early summer, [2021] those who were unvaccinated were 4.5 times more likely than the fully vaccinated to get infected, over 10 times more likely to be hospitalized and 11 times more likely to die, according to the Centers for Disease Control and Prevention.
..... "Vaccination works," Dr. Rochelle Walensky, CDC's director, told a White House briefing Friday. [09/10/2021] "The bottom line is this: We have the scientific tools we need to turn.
..... So-called "breakthrough" cases in the fully vaccinated accounted for 14% of hospitalizations and 16% of deaths in June and July, [2021] about twice the percentage as earlier in the year.[2021]
..... Walensky said Friday [09/10/2021] that well over 90% of people in U.S. hospitals with COVID-19 are unvaccinated.
US opens probe into ram diesel trucks; engines could stall
..... U.S. Safety regulators are investigating fuel pump failure in more than 600,000 diesel Ram trucks that could cause the engine to stall or lose power. the probe covers Ram 2500, 3500, 4500 and 5500 heavy-duty trucks with 6.7-liter cummins turbodiesel engines.
..... The National Highway Traffic Safety Administration says in documents posted on its website Monday [10/18/2021] that it received 22 complaints and two filed reports of engines stalling due to high-pressure fuel pumps failing. Agency documents say it has no reports of crashes or injuries.
Toyota unveils first EV since 2014
..... Toyota, the top-selling automaker in the U.S., is rolling out its first fully electric vehicle in eight years.
..... The company on Tuesday [04/12/2022] unveiled the battery-powered BZ4X small SUV, which starts at $42,000 and can go up to 252 miles per charge.
..... The bZ4X which will be sold globally, adds to the 38 electric vehicle models now on sale in the U.S., with more than 120 expected by 2025.
..... It is Toyota's first EV since 2014, when it last sold an electric version of the RAV4.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
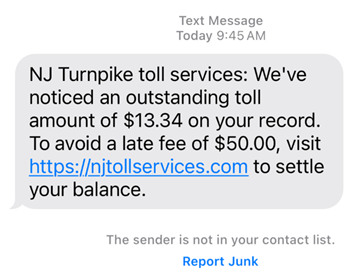
Image 1. SMiShing text message |
|
|
|
Image 2. Malicious landing page impersonating USPS |
|
Image 3. Source: Urlscan.io |
|
|
|
|
|
|
|
|
Phishing website used in this campaign – Source: Cyble
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
“Hi there, gate. This is Glenda and I'm at Healthcare Health Center. Is this Robert? Is this Robert I'm speaking with? All right, perfect. Well, Robert, the reason why I'm calling is to provide your info, information, and options on your Medicare supplemental plan.” |
|
US probes reports of steering glitch on newer Honda Civics
..... U.S. Auto safety regulators are investigating complaints form Honda Civic drivers that the cars' steering can stick, causing a momentary increase in effort and increasing the risk of a crash.
..... The probe by the National Highway Traffic Safety Administration covers an estimated 238,000 Civic from the 2022 and 2023 model years.
..... The agency says it has 145 complaints about the problem, which happens mostly at highway speeds. The complaints came over the past 11 months and occurred mostly on vehicles with low miles.
..... NHTSA has no reports of crashes or injuries from the problem.
..... The company says most of the Civics should be under warranty, and that if any owner feel something is not right, they should contact their dealer.
CDC, FDA say General Mills four linked to salmonella outbreak
..... The Food and Drug Administration and Centers for disease Control & Prevention have linked Gold Medal Unbleached and Bleached All Purpose Flour with a multislate salmonella outbreak. The two agencies announced the finding Monday [05/01/2023] after the FDA found that five of nine cases in the outbreak had exposure to raw Gold Media flour. a sample taken at the General Mills plant in Kansas city, Missouri, was found to have the strain of salmonella affecting people in the outbreak, the FDA said.
..... General Mills issued a voluntary nationwide recall on April 28, [2023] of 2-. 5- and 10-pound bags of the flour with a "Better If Used By" dater of March 27, 2024, and March 28, 2023, according to the recall.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
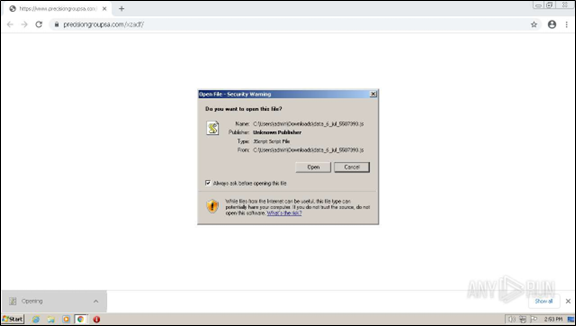
Malicious JScript file. Image Source: Any.Run |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Balsam Hill scam Facebook ad. Image Source: Trend Micro
|
|
|
|
Honda, BMW, Subaru among 528K cars recalled:
By: Zoe Wells
USA Today
..... The national Highway Traffic Safety Administration issued multiple recalls last week, [11/17/2023] nearly 250,000 Honda Vehicles for a manufacturing error in the connecting rod baring.
.....
Are you looking to see if any recalls were issued on your vehicle? If the car isn't listed below, owners can check USA Today's automotive recall database or search the NHTSA's database fro new recalls. the NHTSA website allows you to search for recalls based on your vehicle identification number, or VIN.
..... Here are the vehicles recalls published by the NHTSA from November 11 to 18. [2023]
Honda recall:
Connecting rod bearing error
..... Honda is recalling 248,999 of its 2015-2000 Acra TLX, 2016-2020 Acura MDX, 2016-2019 Pilot, 2017 and 2019 Ridgeline, and 2018-2019 Odyssey error in the connecting rod bearing. The connecting rod bearing in the engine may wear and damage the engine. a damaged engine may cause it to stall, which increases the risk of a fire, crash, and injury, according to an NHTSA report.
..... Dealers will inspect and repair the engine as necessary, free of charge. Owner notification letters are anticipated to go out by January 2, 2024. Should owners require assistance, they can reach Honda customer service at 1-888-234-2138. the recall number are XG1 and GGO.
BMW Recall:
Camshaft timing bolts
..... BMW is recalling 155,627 vehicles because of camshaft timing bolts that can losses. The aluminum bolts on the vehicle that seal the housing for the variable camshaft timing adjustment (VANOS) may gradually loosen over time. If the VANOS that hold bolts loosen, it can increase the risk of injury and crash because the engine may stall, according to an NHTSA report.
.....
Dealers will offer complimentary replacement of the four VANOS bolts. Letters alerting owners will be sent out on December 12. [2023] a second letter will be sent out when the solution is figure out. Owners can get in contact with BMW customer service at 1-800-525-7417.
Recalled vehicles:
* 2010-2012 BMW I Series
* 2010-2012 BMW 3 Series
* 2010-2011 BMW 5 Series
* 2010-2011 BMW X3
* 2010-2011 BMW Z4
Subaru Recall: Rear-view image
..... Subaru is recalling 95,830 of its 2021 Crosstrek, 2022 Forester and 2021-2023 Legacy and Outback vehicles because of review image problems. A defective weld might make some water pour into the inhibitor switch, which can cause it to malfunction. an inhibitor switch that is not functional can result in the failure of reverse lights to illuminate the rearview camera image to display, raising the likelihood of a collision, according to an NHTSA report.
..... Dealers will replace the inhibitor switch at no change. Notification letters will be sent out January 8, 2024.
..... Owners can reach Subaru at 1-800-782-2783. the recall number is WRQ-23.
|
|
|
|
|
|
|
|
|
US probing engine fires in Toyota RAVE SUVs:
..... The U.S. government is investigating complaints of engine compartment fires in Toyota RAV 4 small SUVs. the investigation could affect nearly 1.9 million vehicles.
..... The National Highway Traffic Safety Administration began investigating after getting 11 fire complaints involving the 2013 through 2018 model years.
..... In
documents posted Monday, [03/01/2021] the agency says fires start on the left side of the engine compartment. A terminal on the 12-volt battery may short to the frame, causing loss of electrical power, engine stalling or a fire.
IMPORTANT: Barnes & Noble says shopper info may have been taken in hack:
..... Barnes & Noble said the personal information of its shoppers may have been stolen after its computer systems were hacked.
..... The bookseller told customers in an e-mail Wednesday [10/14/2020] that hackers could have had access to their e-mail address, name, phone number, home address and a list of books or other products they have purchased.
..... The company said hackers didn't access credit card numbers and other payment information because it was encrypted.
..... Barnes & Noble said it learned of the hack on October 10. [2020]
..... Barns & Noble declined to say how many customers may have been affected by the hack.
IMPORTANT: US investigates fire reports in Chevy Bolt electric vehicles:
..... The U.S. government's road safety agency is investigating complaints that the Chevrolet Bolt electric vehicle can catch fire.
..... The probe by the National Highway Traffic Safety Administration covers nearly 78,000 Bolts made by General Motors from the 2017 through 202 model years.
..... The agency says in documents posted on its website Tuesday [10/13/2020] that it has three reports of fires that began under the rear seat while the cars were parked and unattended.
..... One person suffered smoke inhalation.
.... The fire damage appeared to be concentrated in the battery compartment area, spreading into the passenger area.
.... GM says it's cooperating with the probe and conducting its own investigation.
..... "The safety of our products is the highest priority for the entire GM team," the statement said. the company would not comment when asked whether the vehicles should be parked outside until the cause of the fires is determined.
IMPORTANT: US probes Mercedes vans for possible unwanted acceleration:
..... U. S. Auto Safety regulators are investigating speed sensor problems with Mercedes-Benz Sprinter full-size vans that could cause unwanted acceleration.
..... The probe by the National Highway Traffic Safety Administration covers about 160,000 Sprinter 2500 and 3500 vans from the 2011 through 2018 model years.
..... The agency says it has 44 complaints of rear wheel speed sensor problems that caused large fluctuations in speed and erratic transmission shifting.
IMPORTANT: Carnival Corporation hacked: guest and worker information accessed:
..... Carnival Corporation says it was the victim of a ransomware attack that likely got some personal information about the cruise company's guests and employees.
..... The attack was first detected Saturday. [08/15/2020] The attack accessed an encrypted portion of technology systems for one of the cruise line's brands and certain data files were downloaded, the company said in a filing with the U.S. Securities and Exchange Commission.
..... Carnival operates Carnival Cruise Line, Princess Cruises. Holland America Lines and other lines.
Announcement
The OVC Release Fraud Alert:
Scammers Target Senior Citizens, Claim to be DOJ
..... The Office of Justice Programs' Office for Victims of Crime (OVC) released a fraud alert after receiving reports regarding a pishing (voice-phishing) scam in which individuals claiming to represent the Department of Justice (DOJ) are contacting private citizens in order to obtain user's personal information. The scam appears to primarily target senior citizens. Those who receive these or similar calls are urged to avoid providing any personal or financial information and to report these scams to the Federal Trade Commission (FTC) via their website or by calling 877-FTC_HELP (877-382-4357). Fraud can also be reported to the FBI for law enforcement action at www.justice.gov/criminal-fraud/report-fraud . The National elder Fraud Hotline is a resource created by OVC for people to report fraud against anyone age 60 or older. Reporting certain financial losses due to fraud as soon as possible, and within the first 2 to 3 days, can increase the likelihood of recovering losses. For more information about the hotline, please visit stopeldeerfraud.ovc.opj.gov
Data of 10.6 Million MGM Reports Guests
Has Been Discovered on a Hacker forum
WHAT HAPPEN?
..... Data Security researchers discovered an online database containing the personal information of 10.6 million MGM Reports guests, including celebrities, reporters, government officials, and tech company executives, on a hacker forum. The database is reportedly from a security incident that occurred last summer [2019] in which data was obtained through unauthorized access to a cloud server.
Breached data include:
* Full names
* Dates of birth
* Home addresses
* Phone Numbers
* E-mail addresses
..... MGM reportedly contacted affected guests when the incident was discovered last summer, [2019] however the data has now appeared on well-known hacking forums. MGM has said that the exposed information was old and believes that the breached data is from guest stays from 2017 and earlier. While no payment information or passwords are part of the exposed data, the personal information could be used in phishing attacks, password resets, and other nefarious activities.
Honda hit by cyberattack:
..... Japanese carmaker Honda said Tuesday [06/09/2020] it was hit by a cyberattack that disrupted its business in several countries, though it expects the impact to be contained.
..... The company said there was no breach of data, but that it is working to "minimize the impact and to restore full functionally of production, sales and development activities."
..... "At this point, we see minimal business impact," the company said.
..... Production in Japan is back to normal. after being disrupted Monday [06/08/2020 morning and it is also expected to resume Tuesday [06/09/2020] in North America.
..... Production at Honda's U.K. factory in Swindon has been suspended during the COVID-19 lockdown and the attack is not expected to significantly alter tis plans to resume operations this week.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Image Source: WJLA-TV/Renee Roberson |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
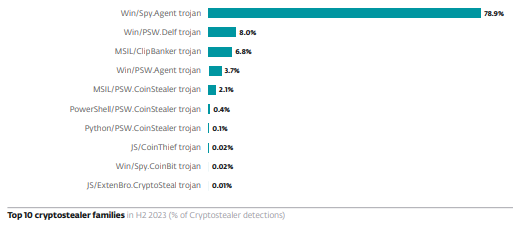
Image source: ESET H2 Threat Report |
|
|
|
|
|
|
|
|
|
|
|
Sextortion and Romance Scams:
Dodging Cupid’s Malicious Arrow
As Valentine’s Day approaches, threat actors may attempt to prey on individuals seeking companionship or romance. The NJCCIC continues to receive reports of sextortion incidents in which victims are threatened with the release of compromising or sexually explicit photos or videos if they do not pay an extortion demand. Some sextortion threats are not credible, as threat actors are unable to provide proof of such photos or videos. However, there is an increase in reported sextortion incidents in which threat actors pretended to be trusting potential love interests. In several recent incidents, threat actors posed as attractive females to target their victims, build trust, and convince them to send compromising or sexually explicit photos or videos.
Threat actors use social engineering tactics to lure their victims via email, text message, chat, and video chat apps (such as Snapchat, WhatsApp, Skype, and Kik), social media platforms (such as Instagram, Facebook, and Wizz), or dating apps (such as Grindr and Hinge). They may initiate communication through one of these platforms and then move to other platforms. They build trust with their victims and convince them to divulge personal information—such as phone numbers, family members, employers, and social media account information—before threatening to post the photos or videos to the victim’s social media platforms or release them to family members, friends, or employers. They may also threaten to upload explicit photos or videos to various pornographic websites if payment is not made. Extortion payments are typically demanded to be sent via Zelle, Venmo, Cash App, MoneyGram, Bitcoin, Coinbase, or gift cards. Similar to sextortion, threat actors may engage in romance scams by posing as potential love interests and building trust with a victim to establish a relationship quickly. Eventually, they may create a fake emergency and request the victim send money to help. They may also encourage victims to make cryptocurrency investments that turn out to be scams
Sextortion and romance scams continue to be successful as threat actors change tactics to coincide with trends and topics of interest to increase their likelihood of a reward or payout. To help counteract these scams, the New Jersey Senate passed legislation last year to make sextortion a third-degree crime punishable by up to five years in prison and a $15,000 fine. For victims who are minors or adults with developmental disabilities, the offense would be a second-degree crime punishable by up to 10 years in prison and a $150,000 fine.
The NJCCIC recommends users educate themselves and others on this and similar scams to prevent future victimization. Please review the Beware of Sextortion and Romance Scams NJCCIC product. The NJCCIC also advises against paying ransoms of any kind, as these scams are typically not considered credible threats unless photos or videos are provided. Users are advised to inspect questionable requests for typical indicators of these scams, exercise caution with unsolicited communications, and refrain from providing photos or videos, personally identifiable information (PII), financial information, or funds. Users are encouraged to report cyber incidents via the NJCCIC Cyber Incident Report Form, the FBI’s Internet Crime Complaint Center (IC3) website, and their local police department. Users are also advised to report scams or abuse to associated email providers, social media platforms, or dating apps, especially if there is a violation of terms and conditions or acceptable use policies.
|
|
From Life Lock & Norton
|
||||||
|
||||||
|
||||||
|
||||||
|
||||||
|
||||||
|
||||||
|
||||||
|
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ransomware Visit: StopRansomware.gov
US intel: Putin misled by advisers - Click Here
8 Ways to Make Your LinkedIn Profile Stand Out - Click Here
Outside Looking In - Click Here
Multiple recalls issued for vehicles - Click Here
AT&T probing data leak affecting millions - Click Here
Deepfakes disgusting - and just beginning - Click Here
Banks: People should stop writing checks - Click Here
Global threat from plastics is growing - Click Here
Drone delivery may become more common - Click Here
Facebook's video player looks to ease sharing - Click Here
No word on closures as Red Lobster seeks buyer, explores bankruptcy - Click Here
16 charged in 'grandparents scam' that stole millions - Click Here
*** Judge in Menendez case: Stop wasting time - Click Here - Not Linked!!
*** Greene to call for Johnson ouster vote - Click Here - Not Linked!!!!
New poll shows Trump leading Biden by 6 points - Click Here
Zillow ad spot fries back at 'Bluey' episode - Click Here
House Dems say Johnson ouster 'will not succeed' - Click Here
Willams-Sonoma fined $3.2M for false claims - Click Here
Fatal crashes spur inquiry into Ford's hands-free driving tech - Click Here
Saying Trump is pro-life is truly 'fake news' - Click Here
Trump to receive $1.17 billion Truth Social stock bonus - Click Here
Trump campaigning from courtroom - Click Here
US announces new curbs on exports of firearms - Click Here
Contrasts seen in Trump Supreme Court, NY cases - Click Here
Donald Trump - Hush Money trial should be televised - Click Here
Biden signs $95 billion foreign aid bill - Click Here
FDA OKs cell therapies for treating earlier stages of type of blood cancer - Click Here
Students miss more school now than pre-COVID - Click Here
Study: chatbots show bis based on prompted name - Click Here
Tesla scraps plans for inexpensive car - Click Here
New student loan forgiveness on tap - Click Here
Trump says he opposes national ban on abortion - Click Here
Special counsel: Reject immunity claim - Click Here
Americans struggling to pay for utilities - Click Here
Biden, Japan leader likely to discuss bullet train idea - Click Here
Collapse puts focus on migrant workers - Click Here
No toxics found in water from ship hitting bridge - Click Here
What the future holds for NJ's Dollar Tree, Family Dollar stores - Click Here
We need millions more FAFSA applications - Click Here
Tupperware Brands faces liquidity crunch - Click Here
Planters looking for its next 'Peanutters' - Click Here - BeAPeanutter.com - by April 14, 2024.
Prosecutors call judge's jury instructions 'wrong' in Trump documents case - Click Here
House Republicans open probe of 'pervasive' antisemitism at Rutgers - Click Here
Sheriff's death puts spotlight on high-stress job and fatality rates - Click Here - Bee note; This is to give some information about menial health. Please call, text 988 or visit 988lifeline.org fro 24/7 access to free and confidential services.
Is that phone call asking about COVID vaccines legitimate? Click Here
Bill includes antisemitism monitor for universities - Click Here
World courts order Israel to halt famine - Click Here
Why are diabetes, obesity drugs so pricey? - Click Here
Avoid using AI with tax preparation - Click Here
Menendez won't appeal court's decision - Click Here
Menendez's defense may target his wife during trial - Click Here
Menendez has raised about $189K for legal defense so far in 2024 - Click Here
Trial fro Senator Menedez and co-defendants delayed - Click Here
Bill to force TikTok sale now tied to foreign aid - Click Here
Senate votes to extend government spying law - Click Here
Musk says Tesla to unveil robotaxe self-driving car - Click Here
Don't respond to 'can you hear me' phone calls - Click Here
Tariff threat comes as election looms - Click Here
Report: Infinite scrolling dangerous for teenage - Click Here
Chief scientist at WHO sounds alarm on bird flu - Click Here
Justices to consider 'ghost guns' case - Click Here
Tesla to drop prices on three models after decline in sales, production miss - Click Here
Instagram influencer Mazini gets 7 years for $8M fraud - Click Here
FCC reinstates net neutrality rules - Click Here
Nursing home law will require more staffing - Click Here
Arizona's fake 2020 electors indicted - Click Here
Trump's promises seem to be at odds - Click Here
Trump looks to Nixon in high court case - Click Here
Trump funnels funds to his businesses - Click Here
Shadow of ex-president's campaign, rhetoric looms large over proceedings - Click Here
Fighting Online exploitation of children - Click Here
US seeks to delay
trial set for May - Click Here
Chemical plants must limit emissions - Click Here
Spying law reignites House GOP infighting - Click Here
Trump posts $175M bond to shield assets - Click Here
Trump sends mixed signals on who is welcome in GOP - Click Here
Judge agrees to shield witness in Trump case - Click Here
Incumbents follow trump on abortion - Click Here
Biden blames Trump for Arizona abortion ruling - Click Here
High-flying Trump stock hits turbulence - Click Here
Many bet on Truth Social as "meme" stock - Click Here
Move to oust Johnson on hold amid 2-233k recess - Click Here
Baltimore bridge salvage work begins - Click Here
Food court crackdown may be coming at Costco - Click Here
6.9M US seniors live with Alzheimer's Click Here
IRS: $1B in unclaimed tax refunds for 2020 to expire - Click Here - deadline May 17, 2024
Breaking down Biden's student debt relief plan - Click Here
New rules take aim at 'gun show loophole; Online sales - Click Here
House GOP in turmoil after vote fails - Click Here
Trump says he wouldn't sign federal abortion ban - Click Here
Trump's gag order for hush money payments trial - Click Here - April 15, 2024
Trump's media company soars in first day of trading on Wall Street - Click Here
Realtor.com adds climate risk to listings - Click Here - Realtor.com
Climate is new factor for region's homebuyers - Click Here
First ever digital SAT exam results posted - Click Here
Collage aid process hits another snag - Click Here
Some cancers afflicting young adults - Click Here
Measles vaccines should last a lifetime - Click Here
Health experts weight in on what vaccines adults need - Click Here
Kids can buy ammo Online, group finds - Click Here
Blame for wave of crimes is misguided - Click Here
WMO issues 'red alert' on climate change - Click Here
US calls a smartphone monopoly - Click Here
Biden cancels billions more in student loan debt for public service workers - Click Here
Student loan default can affect Social Security - Click Here
Counseling center owner admitted health care fraud, feds say - Click Here
Nadine Menendez lawyer may have to testify - Click Here
Primary wins set stage for Biden, Trump rematch - Click Here
Justices weight if officials went too far - Click Here
Joann files for bankruptcy, plans private ownership - Click Here
Trump flip-flops on baning TikTok - Click Here
The 6% real estate commission dead after Realtor group settle lawsuit - Click Here
Companies haven't paid income tax - Click Here
IRS launches free Direct File pilot program - Click Here
Georgia judge dismisses some charges against Trump - Click Here
House passes bill that could ban TikTok - Click Here
Virtual viewing not an option - Click Here
Never fades away - Click Here
Biden, Trump close to clinching races - Click Here
Hur defends his assessment of Biden - Click Here
Menendez set to face new charges at arraignment - Click Here
Sky-high stakes for State of the Union - Click Here
Trump's 'purge' worries some in GOP - Click Here
Can voters tolerate Trump's alleged crimes? - Click Here
Biden says he would sign bill that could ban TikTok in US - Click Here
Drugmaker shames weight loss drug craze - Click Here
Seresto agrees to $15M settlement for pet collars - Click Here - Seresto.com
Supreme Court pauses Texas migrant arrest law - Click Here
Trump fights gag order in NY hush money case - Click Here
Credit card late fees to be capped at $8 - Click Here
January 6 trials could still happen before election - Click Here
Student debt relief delayed for many - Click Here
Student loan firm accused of avoiding calls - Click Here
Feds hit senator with new set of charges - Click Here
Truth Social co-founders sue Trump in Delaware - Click Here
Most teachers discuss race; ewe wan to talk LGBTQ+ - Click Here
Trump firm's former CEO pleads guilty to perjury - Click Here
What expenses qualify for tax breaks? - Click Here
$118B border deal includes Ukraine - Click Here
AT&T offering $5 credit for customers affected by outage - Click Here
Feds poised to make big change to marijuana rules - Click Here
What to know about the changes for the SAT as it goes all digital in March [2024] - Click Here
DOT aims to help airline passengers with disabilities - Click Here
Microsoft chatbot under fire for harmful responses - Click Here
FBI chief expects wave of election threats this year - Click Here
Big Tech pledges deep-fake crackdown - Click Here
More states pass restrictions on sex education - Click Here
Scammers target tax agencies for your infor - Click Here
Amazon sued over surprise Prime charges - Click Here
Free help available for filing tax returns - Click Here
Over 120,000 gun safes recalled - Click Here
Macy's to shut down 150 'under-productive' stores - Click Here
Prosecutor asks for gag order in Trump's hush money case - Click Here
3 congressional fights may affect your finances - Click Here
Trump appeals $45.4M ruling in fraud case - Click Here
NJ property tax Rates found to be highest - Click Here
Justices say kindness helps avoid polarization - Click Here
Georgia prosecutor tries to block lawyer's testimony - Click Here
Biden considering new executive action on border - Click Here
Google suspend Gemini AI chatbot's ability to generate image of people - Click Here
Students can take longer to accept aid offers - Click Here
Hunter Biden lawyer blasts evidence in federal gun case - Click Here
Biden cancels $1.2B more in student loan debt - Click Here
Prosecutors: Biden accuser had 'extensive' contact with Russian intelligence - Click Here
Legal 'gas station heroin," sold in NJ, can causes seizures and death - Click Here
Biden says he'll hit Russia with major sanctions' Click Here
Justices to her smog reduction plan - Click Here
Judicial nominee looks to make history while facing 'bigotry' - Click Here
Haley: Congress 'lying' on border, aid measure - Click Here
GOP grows reluctant to confront Putin - Click Here
Lawmakers seek to close drug company loophole - Click Here
Lawmakers look for backup plan - Click Here
Wind solar power do work in extreme weather - Click Here
Spiting time? - Click Here
Trump threats put troops at risk, NATO leaders says - Click Here
Trump faces action in 5 court cases - Click Here
Fraud appeal likely to argue 'no victims' - Click Here
Needing cash, Trump turns up the sales pitches - Click Here
Menendez wants swift dismissal of case - Click Here
Biden goes on offense in border fight - Click Here
House Republicans vote to impeach Mayorkas - Click Here
Senate backs aid for Ukraine, Israel - Click Here
Dems seek workaround for Ukraine, Israel aid bill - Click Here
Speaking virtually, Austin pledges support for Ukraine - Click Here
Social media helps fuel climate change denial - Click Here
Take steps to avoid falling for romance scams - Click Here
Climate change denial surges Online - Click Here
More tax breaks for parents in the works - Click Here
Videos of layoff experience become latest viral trend - Click Here
Some prosecutors say Hur went too far - Click Here
Multiple states report new cases of measles - Click Here
Nose picking may have link to Alzheimer's disease - Click Here
Writing resume may be most crucial job skill - Click Here
Education officials try to ease FAFSA woes - Click Here
Arguments in insurrection case to begin - Click Here
House rejects push to impeach Mayorkas - Click Here
FBI report: crimes up at schools, colleges - Click Here
Party leaders divided on border deal - Click Here
Appeals Court: No immunity for Trump - Click Here
Trump asks justices to protect his voters' rights - Click Here
Trump's eligibility for election argued - Click Here
No charges sought for Biden over docs - Click Here
Senate advances $95 billion bill to aid Ukraine, Israel - Click Here
Justice Department targets alleged murder-for-hire plot - Click Here
IRS keeping close eye on cryptocurrency earnings - Click Here
History may decide Trump's ballot eligibility - Click Here
Trial date delayed in Trump's federal election case in D.C. - Click Here
Think before sipping from a Stanley tumbler - Click Here
CDC: Syphilis cases at highest level in decades - Click Here
Swift is newest MAGA target - even in NJ - Click Here - Nothing New
Menendez raised additional $195K for defense fund - Click Here
House GOP unafraid to kill border deal - Click Here
House pases bill to expand child tax credit, renew business breaks - Click Here
GM targets return of its hybrids to North America - Click Here
RSV, flu, COVID, stomach virus cases all on the rise - Click Here
Hospitals require masks again - Click Here - New Jersey
Insulin price cap benefits more Americans - Click Here
Watch out for this common Facebook scam - Click Here
CDC issues alert on rising measles cases globally - Click Here
Busy week in Menendez bribery trial - Click Here
Trump vows to appeal $83.3M ruling - Click Here
NH may have shown Trump's vulnerability - Click Here - bee note that the is just informaiton!!!
Talk urging violence doesn't get free speech protection - Click Here
Biden calls for 'massive changes' on immigration, says border is not secure - Click Here
Texas reshapes immigration debate - Click Here
More jobs, but jobless rate goes up - Click Here
Biden expands abortion, contraception protections - Click Here
Trump makes unusual call to unity - Click Here
Appeals court rejects Trump's bid on gag order - Click Here
Court: Feds can remove border wire - Click Here
Daibes gets court date in bank fraud case from 2018 - Click Here
Telehealth guidelines in NJ block best care, suit says - Click Here
Port Authority recovers $25M from toll cheats - Click Here
GOP senators break on border deal - Click Here
Menendez seeks to suppress evidence in corruption trial - Click Here
Legal battles, election dates could conflict - Click Here
With a therapist shortage in New Jersey, can mental health apps Fill the gap? - Click Here
How new parents get tax credits, deductions - Click Here
New FEMA rules aim, to cut red tape - Click Here
All state high school seniors will now get aid application - Click Here - New Jersey
Some useful tips to help you protect your care in frigid winter temperatures - Click Here
Feds charge 3 guards at Passaic County Jail - Click Here
DOJ: Consultant took job to leak Trump tax returns - Click Here
Justice skeptical of Chevron ruling - Click Here
Samsung phones vie to make AI mainstream - Click Here
Georgia DA blasts misconduct allegations - Click Here
Menendez and wife request separate trials - Click Here
Propose expands child tax credit - Click Here
Site targets NJ's stockpiles of reusable grocery bags - Click Here - litterfreenj.com
Gridlock threats student borrowers - Click Here
'People may be surprised' by 1099 form, experts say - Click Here
Rutgers is latest US school to face antisemitism lawsuit - Click Here
Meta to hide posts about suicide, eating disorders from teens. - Click Here
Taxation of Social Security benefits varies - Click Here
Cybersecurity an issues at water utilities - Click Here
Naloxone needed in first-aid kits, say experts - Click Here - New Jersey
Repaying student loans could result in tax break - Click Here
It's time: Menendez, indicted again, must leave office - Click Here
Biden takes fight over border wire to US Supreme Court - Click Here
Menedez's defense may hinge on patriotism - Click Here
Menendez defens himslef on floor of Senate - Click Here
Menendez files to have corruption indictment dismissed - Click Here
FAA starts probe of Boeing's adherence to safety rules - Click Here
Indictment highlights deep ties of Daibes, Menendez - Click Here
North Jersey towns urge Pascrell to support a cease-fire - Click Here
Law could clarify electoral vote count - Click Here
Biden-Trump rematch could shake politics -Click Here - Not Linked!!
Guardrails meant to preserve democracy - Click Here
Trump lied after I found no voter fraud - Click Here
GOP appeals Trump ballot ban in Colorado - Click Here
Menendez accused of influencing Qatar firm - Click Here
Biden takes fight over border wire to US Supreme Court - Click Here
Number of migrants brought by bus to NJ tops 1K - Click Here
Clinton, Trump named in Epstein files - Click Here
US debt hits record $34 trillion - Click Here
Trump sues over Maine ballot action - Click Here
Raskin: Thomas should skip trump ballot cases - Click Here
GOP rivals say they would pardon Trump if elected - Click Here
Ex-Trump aides warn of serious threats if he wins - Click Here
AI systems can detect guns, alert schools - Click Here
Social platforms need hate speech oversight - Click Here
Rural folks feel like they were left behind - Click Here
Experts say work-from-home model will continue - Click Here
Tax deadline is months away, but don't wait to file - Click Here
Trump faces many questions in 2024 - Click Here
What NJ residents need to know on Medicare Advantage - Click Here
Trump facing signs of political trouble in 2024 - Click Here
Hospital tool aims to end pricing surprises - Click Here
IRS delays new rules for payment app users - Click Here
Group calls for change in use of bodycam footage - Click Here
FDA rules change opens up new pool of blood donors - Click Here
The New York Times sues OpenAI and Microsoft over the sue of its stories - Click Here
Prosecutors seek to bar Trump lawyers from injecting politics into trial - Click Here
Immigration court backlog tops 3M cases - Click Here
Advocates criticize border proposals - Click Here
Supreme Court likely to hear ballot issue - Click Here
Few in Colorado joyful over Trump ruling - Click Here
Facial recognition tech banned at Rite Aid - Click Here
White House backs effort on EV charging - Click Here
Impeachment witness: Biden not involved in deals - Click Here
January 6 footage could be game changer - Click Here
Fare Warning - Click Here - New York MTA
US officials say 2022 election were secure - Click Here
Apple pauses certain watch sales over patent dispute - Click Here
Trump asks entire court of appeals to review gag - Click Here
Daibes seeks to postpone his trial - Click Here
Conflict will continue to stir passion on campuses - Click Here
White House involved in border talks - Click Here
Regulations will affect small business in 2024 - Click Here
Trump quotes Putin, evokes fascists at rally - Click Here
Santa, please help Congress protect our kids - Click Here
Some pet meds could harm humans, FDA says - Click Here
Could US economy dodge recession? - Click Here
Feds open investigation into antisemitic incidents at Rutgers - Click Here
House passes defense bill in last-minute spirit - Click Here
Santos lawyer optimistic about plea negotiations - Click Here
Trump denied immunity in Carroll defamation case - Click Here
Supreme Court to hear from January 6 defendant - Click Here
Student loan borrowers keep waiting for answers - Click Here
Supreme Court to consider abortion pill - Click Here
Hunter Biden seeks dismissal - Click Here
Hunter Biden defies GOP subpoena - Click Here
Georgia election worker says she feared for her life over lies - Click Here
GOP impeachment push like Dems', but less transparent - Click Here
Epic Games wins lawsuit against Google - Click Here
Jury seated in Giuliani damages trial - Click Here
Smith asks high court to rule on Trump claim - Click Here
CVS health to alter its drug payment model - Click Here
Why won't the Senate go after Menendez on ethics charges? Click Here
Pandemic led to kids in private schools - Click Here
Most Republicans hope Trump is GOP's nominee - Click Here
Trump says he'll be a 'dictator' only on Day 1' if he's reelected - Click Here
Liz Cheney warns voters must stop Trump from being reelected - Click Here
Why lawmakers are leaving Congress - Click Here
FBI director makes fresh pitch to renew spy program - Click Here
Buying an EV? Make sure to factor charger in cost - Click Here
Check the Online database; unclaimed money could provide a potential; financial windfall - Click Here - New Jersey.
US expanding high-tech cooperation - Click Here
Economists think nation can avoid a recession - Click Here
Trump gag orders difficult to enforce - Click Here
Will Santos ouster save GOP majority? - Click Here
School presidents walk back response on antisemitism - Click Here
Republicans in Senate block aid for Ukraine/Israel - Click Here
NYU faces lawsuit over hate speech - Click Here
Asylum-seekers sue US over Trump, Biden border policy - Click Here
Bergen influencer seek to redevelop school site - Click Here
Apple update may pose safety risk, local police say - Click Here
George Santos expelled from Congress in historic House vote - Click Here
Congress eyeing immigration limits - Click Here
Musk, suing an expletive, says he doesn't care about advertisers that fled X - Click Here
Consumer Rep rots pummels EV reliability - Click Here
Google project could be clean energy milestone - Click Here
Trump lawyers urge NY court to void gag order - Click Here
Lawyers: Trump had basis to question 2020 election - Click Here
Trump floats repealing 'Obamacare' - Click Here
NY's Santos says he will stand for expulsion vote - Click Here
Hunter Biden offers to testify at House hearing - Click Here
Students may soon learn about Sikhism - Click Here
Google to start deleting inactive accounts - Click Here
Digital wallets could face same regulation as banks - Click Here
Toys that can spy on kids are called a growing concern - Click Here
Eight ways residents can get homes ready for winter - Click Here
Phonics is hot again as NJ schools fight COVID learning loss - Click Here
Senate panel issues subpoenas to discuss children's safety Online - Click Here
Decision weakens enforcement of Voting Rights Act - Click Here
Ethics panel finds 'substantial evidence' Santos committed fraud - Click Here - Ethics panel finings
Electric ferries may set a new energy standard - Click Here
Ukraine aid tangled with border policy - Click Here
Toys R Us maybe in midst of resurgence - Click Here - macys.com/toysrus and ToysRUs.com
Government makes more free COVID-19 tests available - Click Here - COVIDtests.gov
UN: World racing past warming limit - Click Here
Supreme Court declines appeal in Chauvin case - Click Here
Cinnamon imports face FDA inspection - Click Here
NJ January 6 suspect a military police officer - Click Here
We can still learn from the wisdom of JFK - Click Here
Is honking horn free speech? High court asked to decide - Click Here
Remote work led to gains for some - Click Here
USDA map helps gardeners keep up with climate change - Click Here
Respiratory illness in dogs investigated - Click Here
Supermarket shoplifters find reusable bags handy - Click Here - A Bee note this is not a thin that shoppers should consider doing!!!!!
No quick fix - Click Here
Roller-Coaster week for Trump, GOP - Click Here - Bee does not look at this as a politician item!!
How will 2024 IRS tax brackets affect you? - Click Here
House dodges government shutdown - Click Here
Feeling sad as winter nears? How to cope with SAD - Click Here
First lady to lead initiative on women's health research - Click Here
Asians, Pacific Islanders face abuse - Click Here
Businesses push back on new NLRB rule - Click Here
Heat records grow as plant roasts - Click Here
Report IDs climate change villains: us - Click Here
Census Bureau: World's population over 8 billion - Click Here
Kindergarten vaccine exemption rates rise i 41 states, CDC finds - Click Here
Meta knows it's harming our kids, so we are suing - Click Here
Change could be coming to real estate commissions - Click Here
Rite Aid is selling 7 NJ leases amid bankruptcy - Click Here
After four-month strike, actors reach $1 billion deal with Hollywood studios - Click Here
FBI searching for Capitol riot suspect - Click Here
The FBI manhunt for Gregory Yetman is over - Click Here
10 alleged Gambino members arrested - Click Here
Will daylight saving time end permanently? A Senate bill would do that - Click Here
Daylight saving time's end provides health benefits, doctors say - Click Here
74% of people in poll want to stop annual clock change entirely - Click Here
Data: More babies dying in 1st year - Click Here
Stores weigh tech's worth - Click Here
Victims of Bergen influencer's alleged scheme speak out - Click Here
3 justices to watch in gun law case - Click Here
2 NJ schools want colleges to show plans for boosting Jewish safety - Click Here
Orsted wants out of $300M forfeiture - Click Here
Johnson's stand on elder benefits unclear - Click Here
Job market shift boosting employers - Click Here
He believes Trump is president - Click Here
What will you pay in NJ for Obamacare in 2024? - Click Here - getCovered.nj.gov - Healthcare.gov
Judge sets rules for juror search in Trump's Georgia trial - Click Here
Danish company pulls out of NJ offshore wind project - Click Here
NJ finds $1M in bad Medicaid claims - Click Here
Students hope app helps make EMT work easier - Click Here
Should government regulate social media? - Click Here
Young employee focused on flexibility - Click Here
Initiative aimed at affordable housing - Click Here
McDonald's ditching its McFlurry "spindle' - Click Here
Michigan clash is free speech test - Click Here
Biden pitching narrower student loan relief proposal - Click Here
Judge to US: Stop cutting razor wire Texas installed - Click Here
FDA warns many eye-drops can cause infections - Click Here
NYC to give free, 1-way tickets to migrants - Click Here
Could daylight saving time be sunsetting in United States? - Click Here
Does ADHA raise risk of dementia? - Click Here
USPS's new policy requires ID verification - Click Here
EPA to propose stiffer lead pipe rules - Click Here
Low EV demand worrying car-makers - Click Here
NJ, other states sue Meta over impact of social media on young - Click Here
USPA touts 600+ arrest in postal crime crackdown - Click Here
Moderates not worried by speaker's vote record - Click Here
Prosecutors ask judge to reinstate Trump gag order - Click Here
Americans using cards may face more fees - Click Here
Medicare Part B cost in 2024 to rise 6% - Click Here
'Dreamers' forming strategy to keep DACA alive - Click Here
Tradition of toy trucks will live on after merger - Click Here - HessToyTruck.com
Trump settles into role of defendant - Click Here
Americans' faith in institutions wanes - Click Here
Senator Clueless? What was Menendez thinking? - Click Here
4 unique gifts for busy professionals - Click Here
Chinese firm Baidu unveiled AI model - Click Here
Europe looking to fight flood of Chinese EVs - Click Here
Amazon tests drones to drop off medicine - Click Here
Amazon delivers meds via drones - Click Here
Poll shows Biden, Trump tied at 37% - Click Here
Reports: Loan plan will help undergrads - Click Here
Real estate investor, influencer charged in scheme - Click Here
Sidney Power pleads guilty in election case - Click Here
Ellis pleads guilty in Georgia election case - Click Here
Rite Aid to close more stores - Click Here
Trial could change search habits - Click Here
Many in state seek stigmatized treatment - Click Here - New Jersey
Fall vaccination season gets underway - Click Here
Student loans forgiven for 804,000 - Click Here
Student loan payments due again - Click Here
Social Security benefits to rise by 3.2% in 2024 -Click Here
ANCHOR payments are released - Click Here - in New Jersey
Pharmacies to offer birth control over the counter - Click Here
Gaetz is helping Biden by sinking GOP's 2024 hopes - Click Here
IRA saving for small-business workers near - Click Here
Biden presses for more student debt relief as payments resume - Click Here
MTA seeks to join NJ's suit against congestion pricing - Click Here
School pandemic dollars wasted on tech? - Click Here
Laws waived for border wall construction - Click Here
AI could help firefighters - Click Here
Hyundai, Kia electric vehicles using Tesla ports - Click Here
US will admit more refugees from Latin America, Caribbean - Click Here
Google hikes price for new Pixel smartphones - Click Here
House in disarray after speaker chaos - Click Here
Toys R Us comeback? - Click Here
Apple to fix problems making iPhone 15s too hot - Check Here
Abortion, gun cases on high court docket - Click Here
Hackers breach 2 casinos in Vegas - Click Here
Google brings AI chatbot into inner circle - Click Here
Who will be the next speaker after McCarthy? - Click Here
Mental health cases for teens in NJ soar - Click Here
Garland says he'd resign if Biden tries to interfere in Trump cases - Click Here
Biden pleads not guilty to gun charges - Click Here
Hunter Biden sues Giuliani, other lawyers - Click Here
Ex-aide: Meadows burned documents in his office - Click Here
Lawyers: Prosecutors want to 'silence' Trump -Click Here
Amazon investing up to $4B in AI startup Anthropic - Click Here
Biden to create climate corps for US - Click Here
Airbnb says it's cracking down on fake listings - Click Here
Trump's shutdown stance clouds debate - Click Here
Ex-lawyer sues Giuliani, alleges $1.36M tab unpaid - Click Here
Impeachment inquiry hearing set in House - Click Here
Florida jury could give edge to Trump - Click Here
Hunter Biden sues IRS over tax disclosures after agent testimony - Click Here
Will SAVE college loan plan help student borrowers? - Click Here
Hate on the rise - Click Here
Averting a shutdown won't be easy on hill - Click Here
Congressional divide starker than ever - Click Here
DACA recipients are left in limbo - Click Here
AI is here - Will journalism ever be the same? - Click Here
TikTok's e-commerce shop launches in US - Click Here
Updated vaccine trio coming soon - Click Here
US approves updated COVID-19 vaccines - Click Here
Should kids get the newly approved COVID booster? - Click Here
ALS patients in NJ cheer iPhone's new voice banking accessibility feature - Click Here
Georgia prosecutors urge one trial for Trump, 18 others - Click Here
Trump won't be tried with attorneys - Click Here
NJ mother taking on Trump, guns and book bans - Click Here
Hunter Biden indicted on federal firearms charges - Click Here
Challenges loom as House returns - Click Here
Smucker to buy Hostess in $5.6B cash/stock deal - Click Here
Consumers should watch out for these new IRS scams - Click Here
COVID-19 side effect - Parents are flexing their power at kids' schools - Click Here
Judge approves Party City's plans to stay afloat - Click Here
RU makes breakthrough in a no-shot vaccination - Click Here
Watchdog describes border wall harm - Click Here
Trump Organization offloads golf course in Bronx - Click Here
McCarthy: Open impeachment inquiry - Click Here
Trump seeks recusal of election case judge - Click Here
Study: HPV shots cut risk of STI, cancer for years - Click Here
Rite Aid said to be filing for Chapter 11 - Click Here
Walmart shopping carts draw complaints Click Here
Congress will try to avert government shutdown - Click Here
Former chief of staff pleads not guilty in Georgia election case - Click Here
Capitol doctor gives McConnell assessment Click Here
Power of attorney a way to help college kids - Click Here
Democrats: IRS free tax filing under fire - Click Here
Cash bail meant to deter wrongdoing - Click Here
Unique academy and educational tracks in schools - Click Here
Google reaches deal in app store lawsuit - Click Here
EPA delays new ozone standards - Click Here
Smith: Trump's comments risk tainting DC jury pool - Click Here
Trump and Hunter Biden are train wrecks - Click Here
Trump's Trials - Click Here
Trump trial in federal election case set for March [2024] - Click Here
Trump denies inflating net worth - Click Here
Trump pleads not guilty in Georgia election case - Click Here
Trump continues drumbeat of election lies - Click Here
Biden is 'old,' Trump is 'corrupt' - Click Here
US, China agree to launch talks on export controls - Click Here
How to prepare kids for flu, COVID and RSV - Click Here
FDA issues warning letters to three infant formula makers - Click Here
Amazon CEO warns employees of return to office - Click Here
Georgia jail where Trump will be booked is problematic - Click Here
Prosecutors say witness retracted false testimony - Click Here
Giuliani turns himself in on Georgia election charges - Click Here
Trump to surrender at Georgia jail - Click Here
Officials warn of scams targeting Maui donations - Click Here
Hawaii vows to protect local landowners - Click Here
Study: Arthritis drug could boost morning-after pill - Click Here
Colleges seek to 'ChateGPT-proof' assignments - Click Here
Involving parents in schools is good for NJ - Click Here
Sopranos were better at evading RICO than the Donald - Click Here
Trump, allies repeat election lies - Click Here
Fake reviews could face fines - Click Here
Everyone can save for retirement with Roth IRAs - Click Here
Amount down, but spotted lanterflies are still around - Click Here - New Jersey
The next federal debt crisis is looming - Click Here
Elite colleges face scrutiny over legacy admissions - Click Here
Voters many grow tired of trump's trails - Click Here
Alzheimer's drug often not covered - Click Here
Costly airline phone scam is clipping travelers' wings - Click Here
Amazon warns of new Online shopping scams - Click Here
QR code scams can prove very costly to victims - Click Here
Lawsuits against real estate influencers climb to 11 - Click Here
Poll: US divided over Trump cases - Click Here
Prosecutors say Biden gun charges deal dead - Click Here
Georgia case's size an issue for both sides - Click Here
Trump assails election case judge - Click Here
Court site publishes, removes, Trump charges - Click Here
Trump and 18 Allies charged - Click Here
Indictment may be Trump's biggest - Click Here
How RICO law affects Trump case - Click Here
UBS settles 2007 mortgage fraud lawsuit - Click Here
For Treads, the real rival remains TikTok - Click Here
Hunter Biden's lawyers: Part of peal deal still valid - Click Here
Prices soar for Medicare drugs - Click Here
DC National Guard shakeup coming - Click Here
Can the First Amendment bend? - Click Here
Offshore wind would hurt ordinary people - Click Here
Is AI's hallucination problem fixable? - Click Here
DOJ facing biggest test in its history - Click Here
Ex-NYPD head meets with Jack smith's team - Click Here
WeWork not sure it can stay in business - Click Here
Zoom wants its workers back in office part time - Click Here
What to know before renting an apartment - Click Here
New Jersey commissions will study social media's impact on children - Click Here
Passaic County surrogate's make-a-will events reach hundreds of residents - Click Here
Malloy's parents, district settle suit for $9.1M - Click Here in New Jersey
What's next in Hunter Biden case? - Click Here
Hunter Biden's former business partner testifies - Click Here
Amazon offering video telemedicine nationwide - Click Here
Trump threatens House Republicans - Click Here
Prolific lies - Click Here - New Jersey
Blind Spots - Click Here - New Jersey
Will newest charges change minds of Trump's supporters? - Click Here
Prosecutors may be seeking quick trial - Click Here
Lawyers hints at 1st Amendment defense - Click Here
Trump backers react to charges - Click Here
2024 could mean presidency or prison - Click Here
Pence crucial in Trump indictment - Click Here
Indictment details fake electors scheme - Click Here
More legal trouble for local real estate influencers - Click Here
Many remain loyal to Trump despite latest legal issues - Click Here
Trump's alleged co-conspirotors pose threat if they flip - Click Here
Many January 6 [2021] defendants plead guilty - Click Here
Biden looks to provide heat relief - Click Here - heat.gov
Automakers to build EV charging network - Click Here
Trump says his lawyers met with prosecutors - Click Here
When hackers get your email, they can do financial damage - Click Here
Ground beef from NJ ShopRites is linked to salmonella - Click Here
Ways to stay cool in North Jersey amid looming heat wave - Click Here
Hunter Biden pleads not guilty to 2 tax crimes - Click Here
Giuliani concedes he made false statements - Click Here
Study: Climate change fuels July heat - Click Here
A plea for help - from 911 employees - Click Here
Proposal would boost mental health care - Click Here
To what degree will voters care about climate? Click Here
Funding, compassion must drive opioid fight - Click Here
Musk reveals 'X' logo to replace Twitter's blue bird - Click Here
Amazon asks some corporate workers to relocate - Click Here
Child tax credit could be made permanent - Click Here
White House launches cybersecurity labeling - Click Here
Influencer face allegations of fraud - Click Here
Convicted Ponzi schemer faces new chargers - Click Here
Trump facing mounting legal woes - Click Here
Target letter hings inquiry is zeroing in on Trump - Click Here
AI for rents: This chatbot has answers for those new to the market - Click Here
Judge upholds $5M jury verdict against Trump - Click Here
White House takes on corporate merger, more - Click Here
Want to be a social media authority? FDU starts new program - Click Here
Debate over definition of antisemitism hits home - Click Here
Trump says he's a target of 2020 election investigation - Click Here
NJ has among the most personal injury lawsuits in the country - Click Here
Can you recycle pizza boxes? Click Here
Dos and Don't as a college grad moving home - Click Here
Lawsuit seeks to end terror watch-list - Click Here
Judge to take stage in Trump case - Click Here
Second Alzheimer's drug can help slow progression - Click Here
Poll: Many pessimistic about democracy - Click Here
Why the GOP is losing Gen Z - Click Here
Updated criteria for new FBI HQ site announced - Click Here
Many in US working less than pre-COVID - Click Here
FTC's sting aims to stop Online crooks - Click Here
Rutgers governor [NJ] vote to merge 2 medical schools - Click Here
Poll: Few Back full abortion bans - Click Here
Director defends FBI against GOP criticism - Click Here
FDC OKs over-the-counter birth control - Click Here
Ex-Trump supporter sues Fox News for defamation - Click Here
Senators call for justices to follow ethics code - Click Here
Trump lawyers ask judge to postpone Florida trial - Click Here
Trump talks indictments, election as he promotes NJ golf event - Click Here
Valet pleads not guilty in classified documents case - Click Here
Latest tax scam promises help with refund - Click Here
Army major from NJ charged with defrauding Gold Star families - Click Here
Asian Americans Feel targeted by law - Click Here
New pay for NYC app-based food delivery workers delayed - Click Here
Special counsel's Trump probes cost more than $9M - Click Here
Guess who could be coming with your dinner - Click Here
Costco cracks down on membership card sharing - Click Here
GM Energy's new products can help power your home - Click Here
Meta takes aim at Twitter as Threads makes debut - Click Here
Parts of warrant affidavit unsealed in Trump case - Click Here
Trump valet pleads not guilty in documents case - Click Here
Pentagon plans tighter controls on classified info - Click Here
Pentagon tightening security after docs leak - Click Here
World's first flying car gets approval - Click Here
Twitter users, advertisers react to platform changes - Click Here
Power problems reported in Hyundai SUV - Click Here
Ruling says race cannot be factor in college admissions - Click Here - 06/29/2023
Supreme Court denies Biden's Student Loan Forgiveness - Click Here - 06/30/2023
Sherrill bill promotes tutoring to address pandemic learning loss - Click Here
CDC reprots 1st US spread of malaria in 20 eyars - Click Here
US regulators target bogus Online reviews - Click Here
Climate change effects getting worse - Click Here
Tips to make a computer run more smooth - Click Here
FDA OK s IV gene therapy to treat severe hemophilia - Click Here
Poll: Trump's GOP support dips - Click Here
Court rejects novel legislative theory - Click Here
Big Tech layoffs give other sectors an opening - Click Here
Watchdog alleges theft of COVID aid - Click Here
Supreme Court dismisses Trump hotel lease lawsuit - Click Here
Ford EV battery plants to get sizable loans - Click Here
5 things to know about plan to cut taxes for NJ seniors - Click Here
Microsoft confirms attacks on servers - Click Here
About 1.5 million lose Million lose Medicaid - Click Here
Booker touts measure to protect LGBTQ+ people from discrimination - Click Here
Energy CEO wants to build a better battery - Click Here
Amazon's once-reliable cloud business slows Click Here
Here's why ' filed lawsuit against Google - Click Here
Use tech to reduce summer brain drain on kids - Click Here
Capitol rioter given 14 days of jail time - Click Here
Students feel 'unsupported' at colleges as antisemitic crime rises - Click Here
'Fighting with love' - Click Here
Cybersecurity company details big Chinese hack - Click Here
Organization: ;GBTQ+ amercements under attack - Click Here
Supreme Court to hear Trump trademark case - Click Here
SEC lawsuits show unease with crypto - Click Here
'But most of all I'm human' - Click Here
Dems frustrated by food aid changes - Click Here
Trump hearing likely to be spectacle - Click Here
Trump escalates attack on case - Click Here
Former president pleads not guilty to 37 counts - Click Here
Shadow of Nixon hovers over another ex-president's retreat to NJ - Click Here
Trump tees off in golf club speech - Click Here
Former president calls charges 'fake' in return to New Jersey - Click Here
How much prison could Trump face? Click Here
Is Trump's obsession with revenge a viable political strategy! - Click Here
New round of Trump 'truth or dare' after indictment - Click Here
GOP rallying cry: 'Stand with Trump' - Click Here
Trump trial in documents case scheduled for August 14 [2023] - Click Here
Florida court date for Trump's valet postponed - Click Here
Biden's son to plead guilty in tax case - Click Here
Dems downplay Hunter Biden's deal - Click Here
Report says Alito accepted vacation from GOP donors - Click Here
Company says it can't ensure safety of air bags - Click Here
FTC: Amazon enrolled users into Prime without consent - Click Here
Cases of check fraud escalate dramatically - Click Here
COVID-19 made one thing clear - Click Here
Windows Copilot lands AI capability on your PC - Click Here
Are right-wing attacks on press protections really just attacks on democracy? - Click Here
Why do the feds care about Trump's ties to LIV Golf? - Click Here
Shared concern - Click Here
Trump's legal team, prosecutors spar - Click Here
Ex-Santos aide says he got his job through payments - Click Here
FBI director Wray may be held in contempt of Congress - Click Here
3 signs you may need a credit card hiatus - Click Here
If your child is a bully, psychologist says gently find out why - Click Here - StopBullying.gov
New law allows NJ drivers with autism to not it on licenses - Click Here
Free steering-wheel locks in NJ for Kia, Hyundai models at risk from TicTok - Click Here
NJ boosts telehealth counseling services - Click Here
US coming after January 6 rioters' haul - Click Here
Mar-a-Lago probe shows signs of winding down - Click Here
Poll: Biden weak on economy, guns - Click Here
Postal workers conned by cyber scam are irate - Click Here
FDA approves nasal spray to reverse opioid overdoses - Click Here
Lawmakers seek to put AM radios in every vehicle - Click Here
Suits vs. gun industry face hurdles - Click Here
Vice Media files for Chapter 11 bankruptcy - Click Here
Durham: FBI's Trump-Russia probe flawed - Click Here
Twitter's account purge includes deceased users - Click Here
Durham report details 'flawed' probe - Click Here
Case involving abortion pill moves to appeals court - Click Here
Not enough progress made to curb inflation - Click Here
Proud Boys' Tarrio guilty of conspiracy Click Here
Source says Biden would veto GOP migrant bill - Click Here
Trump digs in on election untruths - Click Here
What's replacing Bed Bath & Beyond? - Click Here
Bed Bath & Beyond to pay severance to 1,300 workers - Click Here
Alleged leaders of multi-state car theft ring indicted in federal court - Click Here
Senators seek to protect kids Online Click Here
Feds: Abortion denial in emergency illegal - Click Here
New Jersey's MVC starts offering vehicle registration display on digital platforms - Click Here
Garden State Plaza implements chaperon rule - Click Here - New Jersey
Surveillance law's future unclear - Click Here
Group calling for end to watch-list - Click Here
US, Mexico agree on tighter border policies - Click Here
Don't learn the hard way: Common items can prove deadly for your dog - Click Here
House votes to restore solar tariffs - Click Here
Ocean temps shockingly high, experts say - Click Here
Liquidation sales for Union-based retailer set to start Wednesday - Click Here 04/26/2023
Bed Bath & Beyond bankruptcy saddens shoppers - Click Here
GM, Samsung plan new EV battery cell factory in US - Click Here
Appeals court says Pence can testify - Click Here
Immigrants are easing worker shortage - Click Here
Biden: 'We're making real progress' - Click Here
Census considers ending question about ancestry - Click Here
US officials seek to crack down on harmful AI products - Click Here
Firearm detections on the rise in airports - Click Here
Lawyer: Proud Boys leader is scapegoat - Click Here
We must protect the First Amendment from threats - Click Here
Commonsense fixes to gun violence in US - Click Here
Fox parts ways with Carlson - Click Here
Fox hosts avoid Carlson's name after his ouster - Click Here
Settlement by Fox casts shadow - Click Here
House passes trans athlete ban for girls; women's teams Click Here
Supreme court won't block $6B debt relief settlement - Click Here
Menendez urges fix for State Department's passport delays - Click Here
Appeals court halts GOP questioning of Pomerantz - Click Here
Poll: NY least of Trump's troubles - Click Here
High court holds off on abortion pill ruling - Click Here
Judge: House GOP can question ex-prosecutor - Click Here
2 accused as secret Chinese police in NY - Click Here
Trump forum a test for CNN, Collins - Click Here
Anti-abortion group aligns with Trump - Click Here
China says US claims of police"groundless' - Click Here
Biden signs order to boost child care access - Click Here
Tax breaks lure clean tech companies to US - Click Here
Abortion pill federal court rulings muddy the debate - Click Here
Plan aims to protect abortion patients' records - Click Here
DOJ to ask for hold on abortion pill barriers - Click Here
Morning-after-style pill seen as tool to fight rising STDs. -Click Here
Lessons from NJ Proud Boy's January 6 [2021] sentencing - Click Here
No driver? No problem - Click Here
Test detects Parkinson's before symptoms appear - Click Here
Abortion bans raise fear in GOP - Click Here
Top 5 skills to Highlight on Your Resume - Click Here
Great part-time jobs for retirees - Click Here
Resources for care of homeless seniors lacking - Click Here - New Jersey
At-home care options for seniors in NJ - Click Here
Where the Heart Is - Click Here
Some tips on fighting elder fraud - Click Here
Technological difficulties - Click Here - NJIT
Keeping in touch - Click Here
Democracy at stake' in Trump investigations - Click Here
Mug shot as a political boost? Some have tried - Click Here
Tsunami of legal challenges expected - Click Here
'First matter: Trump arrest is a political earthquake - Click Here
Trump's legal issues present never-asked questions to ponder - Click Here
Former prosecutor in Trump case subpoenaed - Click Here
After arrest, Trump revives election lies - Click Here
Barr: DOJ could have 'very good evidence' - Click Here
Bragg sues House leader over inquiry - Click Here
Ex-president answering question in fraud lawsuit - Click Here
TikTok scrutinizing continues - Click Here
Some in Congress defending TikTok - Click Here
Congress confronts limits of gun law - Click Here
Medicare, Social Security could fall short, report says - Click Here
House GOP OKs bill to unleash' energy - Click Here
GOP lawmakers accuse Fed of being lax before bank failure - Click Here
Starbucks CEO defends his union stance before Senate - Click Here
Deadly 'superbug' fungus is spreading CDC warns - Click Here
Possible deadly fungus spreading - Click Here
WeightWatchers set to add anti-obesity medication - Click Here
NJ DMV working to help drivers obtain Real ID - Click Here - REALID.nj.gov
Parents needs a digital-age reboot, say some New Jersey mental health doctors - Click Here
Potential TikTok ban stirs up passions among users - Click Here
Fix red flags that could result in audit - Click Here
Tips on how to care for an older relative from afar - Click Here
Can Solar Farms produce food, too? - Click Here
5 tips on Negotiating Your New Job Salary - Click Here
TikTok CEO faces off with Congress - Click Here
8 tips on How You Can Prioritize Finding The Right Job in 2023 - Click Here
8 Illegal Job Interview Questions And How to Handle Them - Click Here
How to help older NJ drivers decide to give up the car keys - Click Here - New Jersey
Prosecutors rest in Proud Boys trial - Click Here
Data: Women outnumbered as execs - Click Here
Why aren't we giving teens real mental health help? - Click Here
More Americans dying in childhood - Click Here
EPA to limit 'forever chemicals' in water - Click Here
Call and Response - Click Here - In New Jersey
Long-used abortion pill is under threat - Click Here
EV charging network gets $2.5B add equity - Click Here
Panel subpoenas files of Hunter Biden's associates - Click Here
Banks are safe, Biden assures US - Click Here
'Forgotten Middle' - Click Here
Is there a federal inheritance tax? - Click Here
Congress health data breach creates huge risks - Click Here
Sicknick family blasts Fox News' Carlson - Click Here
Attacks, investigations test FBI - Click Here
Hicks meets with NY prosecutors - Click Here
China officials decries US policy - Click Here
Now is the time to squash spotted lanternfly eggs - Click Here
Navigating world of elder care can be overwhelming - Click Here
Nations reach accord to protect marine life on high seas - Click Here
Race on to boost EV range in cold - Click Here
Justice Department says police can sue Trump over January 6 - Click Here
Spotting fatigue early can be key to recovery from long COVID - Click Here
TikTok sets new default time limits for minors - Click Here
IMPORTANT: Landlords warned about bias toward ex-inmates - Click Here in New Jersey
China dismisses FBI statement on COVID-19 lab leak theory - Click Here
Justices put student loan forgiveness to test - Click Here
Biden warns of GOP's plans for health care cuts - Click Here
Take these steps to plan long-term care for an elderly relative - Click Here - New Jersey
NJ consumers lost $231 million to fraud last year, [2022] FTC reports says - Click Here
Should you Use Recruiter/Staffing agencies in a Job Search? - Click Here
Teen depression focus of state bill [NJ] - Click Here
Jewish community vigilant as group pushes 'hate' - Click Here
Extremism-linked mass killings have spiked - Click Here
Those who want jobs in New Jersey's cannabis field can start with course - Click Here
Morris district alleges social media harm to students - Click Here - New Jersey
Release of January 6 footage decried - Chick Here
Make your credit cards less vulnerable to fraud - Click Here
Record 6,542 guns intercepted at airports - Click Here
TikTok ban proposed amid tensions with China - Click Here
Sherrill resumes drive for bipartisan auto-theft bill - Click Here
Why are mass shootings the new normal? - Click Here
How AI will change future of health care - Click Here
Choosing the Best Reference for Your Job Application - Click Here
Seeking a change in US census reporting - Click Here
What company changes mean for your home loan - Click Here
Turmoil in courts on gun laws after court's ruling - Click Here
Panel backs moving Narcan over the counter - Click Here
DOJ giving states $231M for gun violence prevention programs - Click Here
White House: Tesla to make EV chargers available to all - Click Here
Low on cash? give these tech freebies a try - Click Here
Tips on Choosing the Best References - Click Here
Company CardBro makes sending greeting cards easy - Click Here
Why many are choosing Medicare Advantage - Click Here
NJ residents need to set preparedness plans - Click Here
FBI looking into NJ veteran's claims against Santos - Click Here
IMPORTANT: The Supreme Court in a 5-3-1 vote overturn Roe v. Waye at 10 AM.!!
China conducted spy balloon work for years, Pentagon says - Click Here
US: Balloon set up to collect lintel - Click Here
6 Chinese entities restricted by US - Click Here
Is tipping getting out of Control? - Click Here
Yes you do need to go back to the office - Click Here
Bills seeks to protect seniors, people with disabilities from scammers - Click Here
Clinton back at WH to push paid leave - Click Here
GOP-led panel targets COVID-19 aid for review - Click Here
WHO chief: COVID-19 nears inflection point - Click Here
12 NJ mayors call for offshore wind pause - Click Here
A Quick, comprehensive Guide to Employee Engagement - Click Here
New idea: Brining your infant to work - Click Here
Want fewer shootings" Pass tougher gun laws - Click Here
5 Tips on Negotiating Your New Job Salary - Click Here
Asian Americans discuss what it's like to live in US, New Jersey - Click Here
Need a US passport? Here's what to know - Click Here - www.us.gov/passport
Crypto firms acted like banks, then collapsed - Click Here
Lawmakers make move on insurrectionists - Click Here
4 Oath Keepers convicted of seditious conspiracy - Click Here
Senators blast Ticketmaster 'mess' after Taylor Swift fiasco - Click Here
US proposes once-a-year-COVID-19 vaccination booster shots - Click Here
Biden's next task: Enticing Americans to buy green - Click Here
Amazon adding new drug program to its offerings - Click Here
Tax the rich? Liberals renew push for state wealth taxes - Click Here
Prosecutor: Oath Keepers saw January 6 riot as triumph - Click Here
Party City, based in North Jersey files for Chapter 11 - Click Here
Explosive, Flammable, Carcinogenic - Click Here
Dangerously close to home - Click Here
Drilling for worst disasters imagined - Click Here
Pause sought in wind farm plan - Click Here
From Brink of Disaster - Click Here
NJ's industrial history peppered by chemicals disasters - Click Here
Booker calls on EPA to strengthen chemical safety rules - Click Here ]
Groups: 'No evidence' offshore wind killed whales - Click Here
Strategies to improve your ability to focus - Click Here
Speaking from experience - Click Here
How to pay transparency may affect your job search or raise - Click Here
Garland initiates Biden probe - Click Here
Idaho stabbing suspect to face hearing in June - Click Here
Proud Boys sedition trial opens two year after January 6 [2021] - Click Here
Biden inspects busy Texas crossing - Click Here
Mexico may accept more expelled migrants - Click Here
GOP pushes anti-abortion measures in US House - Click Here
Justices: NY can enforce gun law during lawsuit - Click Here
Schools sue tech giants over social media harm - Click Here
A new side of gaming - Click Here
Drug that slows down Alzheimer's hits market - Click Here
US appeals court blocks ban on rapid-fire 'bump stocks' - Click Here
Marijuana addition is a real thing, and here's what NJ should know - Click Here
Flu, COVID, RSV bring child care disruptions - Click Here
FTC proposes new rule that would prevent employers from imposing non-compete clauses - Click Here
Slaying suspect to be extradited - Click Here
FTX founder Bankman-Fried pleads not guilty to fraud charges - Click Here
Brian's Legacy - Click Here
FTX's collapse mirrors 18th-century scandal -Click Here
This former Trump aide from NJ set an example the GOP should embrace - Click Here
Court keeps immigration limits in place indefinitely - Click Here
No-nonsense judge takes over Bankman-Fried case - Click Here
RV slump may be warning of recession - Click Here
Video game workers form Microsoft's first US labor union - Click Here
6 ways to make extra money in retirement - Click Here
Microsoft to fight over $68.7B video game deal - Click Here
SEC says it's not violating Musk's free speech right, but doing its mandate - Click Here
US court rejects maintaining Title 42 - Click Here
Court pauses Biden effort to end Title 42 immigration policy - Click Here
FBI Online 'sextortion' of teen boys is soaring - Click Here
Migrants wait for US to lift limits - Click Here
Congress moves to ban TikTok from US government devices - Click Here
Crypto's ties to sports raise ethical questions - Click Here
Anti-LGBTQ rhetoric Online spurs fears - Click Here
Real ID deadlines pushed back 2 years to May 2025 - Click Here
Buyers Beware - Click Here - SaferProducts.go
Amtrak unveils newest trains - Click Here
More migrants released to come as restrictions end - Click Here
Biden renews call for assault weapons ban - Click Here
How to ask for what you want before taking a job - Click Here
Biden signs bill to protect same-sex marriage - Click Here
Former FTX CEO hit with 8-count indictment - Click Here
Merk, Moderna say vaccine for skin cancer shows progress - Click Here
Will your remote job stay that way? - Click Here
Real estate scams on rise - Click Here
Biden restarts task force on immigrants - Click Here
Biden signs law limiting use of nondisclosure deals - Click Here
Justices to hear major immigration case - Click Here
Justices weigh deportation policy - Click Here
White House tackles antisemitism at forum - Click Here
Stakes are high in gay rights Supreme Court case - Click Here
Supreme Court weights 'most important' case on democracy - Click Here
High court justices hear religious rights case - Click Here
Protecting abortion access hits roadblocks - Click Here
Meta board urges changes to VIP system - Click Here
Study: US gun death rates hit highest levels in decades - Click Here
Experimental drug appears to slow Alzheimer's - Click Here
Chinese Americans keeping close eye on unrest - Click Here
Stopping the chain reaction of gun violence - Click Here
How often do mass killings happen at work - Click Here
States move to keep court from lifting Trump asylum policy - Click Here
This is the most important question you'll get asked in a job interview - Click Here
Judge orders Amazon to stop retaliations against organizers - Click Here
HBCU files complaint, seeks review of bus search - Click Here
New legislation puts greater restrictions on toy guns in NY - Click Here
COP27 concludes with no progress on emission cuts - Click Here
In UN climate deal, cash, no emission cuts - Click Here
Jack Daniel's asks justices to hear dog toy dispute - Click Here
'Zombie Debt' Catches homeowners off guard - Click Here
Same-sex marriage bill clears key Senate hurdle - Click Here
Stakes are high in gay rights Supreme Court case - Click Here
Airbnb aims to convince more people to rent out their homes - Click Here
Biden's student loan plan blocked again - Click Here
Pearl River's Pfizer site leads on RSV vaccine work - Click Here
40 states settle Google location-tracking charges - Click Here
Walmart offers to pay $3.1B to end opioid lawsuits - Click Here
Supreme Court rejects hearing another bump stock ban case - Click Here
Supreme Court's election case is test of public trust - and democracy - Click Here
World's shipping industry changed overnight - starting in Jersey - Click Here
Tesla robot walks, waves but doesn't show off complex tasks - Click Here
Climate woes bad and getting worse faster - Click Here
Vonage hit with penalty over cancellations - Click Here
Medicare enrollees warned about schemes - Click Here
Secret language helps child predators avoid detection - Click Here
Homebuyers suddenly calling the shots - Click Here
FBI warns of 'broad threat' to synagogues - Click Here
CDC softens guidelines for prescribing opioids - Click Here
CVS, Walgreens announce opioid settlements of $10B - Click Here
Penn Station remodeling project debate lands in court - Click Here
Why might live election results fluctuate in US? - Click Here
Justice take up affirmative action cases - Click Here
Move aside, BA.5: New variants are gaining ground - Click Here
Fraud, scam cases increasing on Zelle, Senate report finds - Click Here
Chinese officers changed in plot to obstruct US Huawei probe - Click Here
Later in life,lack of sleep may pose risk to health, study says - Click Here
Climate change is not a new concern - Click Here
EPA awarding nearly $1B for electric school buses - Click Here
Judge let's New York's new gun laws remain temporarily - Click Here
NY AG moves for court oversight of Trump Organization - Click Here
Delta invests $60M in air taxi developer - Click Here
Judge halts key parts of NY's new gun law - Click Here
White House unveils guidelines, plan for AI equity - Click Here
Global database of fossil fuels launched - Click Here
STD rises spurs calls for changes - Click Here
The 'Google' of Gen Z - Click Here
'Credit invisibles' about to be seen - Click Here
Biden pledges to make federal fleet electric faces slow start - Click Here
Sparking changes: Plans for EV stations approved - Click Here
Special master signals quick reviews - Click Here
House OKs election law overhaul - Click Here
Here's how claiming 'unclaimed property' really paid off for me - Click Here
Calls to suicide prevention hotline rise after move to 988 number Click Here
4 non-investment question to ask an adviser before retiring - Click Here
Activists raise alarms about 988 suicide hot-line - Click Here
GOP's Graham seeks federal abortion ban - Click Here
3 charged in broad hacking campaign - Click Here
Biden signs 'burn pit" aid for vets - Click Here
4 things to know about working past age 65 - Click Here
Congress has ways to keep secrets safe - Click Here
Inflation is changing job search - Click Here
Spotted lanternfly questions answers - Click Here - New Jersey
Biden signs executive order to protect travel for abortion - Click Here
Senate OKs aid for vets exposed to burn pits - Click Here
CVS to buy home-health provider Signify for $8B - Click Here
Juul to pay nearly $440M to settle states' teen vaping probe - Click Here
Test of first possible Lyme vaccine in 20 years begins - Click Here
New Online dashboard helps flyers with delays, cancellations - Click Here
Bannon expects new criminal charges in NY - Click Here
Bannon faces money laundering, fraud charges - Click Here
GM's next EV aims at mainstream buyers - Click Here
ALS drug gets second review at FDA meeting - Click Here
China accuses Washington of cyberspying on university that does military research - Click Here
These 9 tips help make more money in your small business - Click Here
Even mile COVID cases can result in symptoms that persist, study finds - Click Here
New minimum? Job seekers increasingly demand $20 an hour - Click Here
FDA chief: Long-awaited opioid review continues - Click Here
New York to restrict gun carrying - Click Here
LG, Honda to set up US joint venture to make EV batteries - Click Here
Just starting out? Learn from our mistakes - Click Here
Drugmaker Teva latest to settle opioid lawsuits nationally - Click Here
Health news has some brains too clogged to think - Click Here
FTC looking at rules to corral tech firms' data collection - Click Here
Court undermines efforts to deter violence - Click Here
AR-15-style guns bring in over $1 billion over last decade - Click Here
Gun violence research takes off across US - Click Here
Polio outburst reveals rare risk of oral vaccine - Click Here
In poll, 2 in 3 favor term limits for Supreme Court - Click Here
Biden signs $280B CHIPS act in bid to boost US over China - Click Here
Climate, health bill a Biden win - Click Here
Video games normalize violence - Click Here
Biden announces modest climate actions, pledges more to come - Click Here
Social media influencers change how you dine out - Click Here
Many question value of college in America - Click Here
House OKs bill to protect contraception - Click Here
AP-NORC poll: Majority in US want legal abortion - Click Here
Experts warn domestic violence is major concern - Click Here
House passes same-sex marriage bill - Click Here
Battle lines from over drug price curbs - Click Here
4 the future? - Click Here
Study: rich nations caused climate harm to poorer ones - Click Here
Docs 'must offer abortion if mother's life at risk - Click Here
BA.5 makes up majority of state's COVID cases - Click Here - www.covid.gov/tests
LGBTQ hate abounds on social media, report says - Click Here
Democrats stress security as computer chips bill stalls - Click Here
Biden celebrates of new gun law clouded - Click Here
FDA to weigh birth control sold without prescriptions - Click Here
House panel looking into extremist ties - Click Here
'Buy now, pay later? One missed payment could mean costly debt - Click Here
The Internet could help or hurt women who are seeking abortion - Click Here
Women of color will be impacted by Roe ruling - Click Here
Courts move puts Senate back in play - Click Here
Abortion ban could affect OB-GYN training - Click Here
High court's abortion ruling sets off new court fights - Click Here
Supreme Court sides with coach who sought to pray after game - Click Here
Poll: Many won't rely on virtual options in future - Click Here
Judge's ruling favors opioid distributors - Click Here
Adoption is not a panacea - Click Here
Biden signs landmarked gun bill - Click Here
Gun ruling could right racial wrong - Click Here
Join our pledge to Democracy - Click Here - www.teamdemocracy.org
'Chaos of emotions' fills Capitol after historic rulings - Click Here
'Let My People in' - Click Here
US to issue monkeypox vaccine as NJ reports 4 probable cases - Click Here
FDA bans Juul vaping products - Click Here
Supreme Court strikes New York gun law - Click Here
Bipartisan gun bill on road to passage - Click Here
NOTICE: The Supreme Court struck down New York State Strict Gun Laws
Senators Compromise on gun bill - Click Here
Dining changes: Restaurants say robot waiters to stay - Click Here
Justices: Religious schools can get aid - Click Here
Internet Explorer finally sent to dustbin of software history - Click Here
Body armor rules miss vest worn by alleged NY shooter - Click Here
Supreme Court rejects Bayer bid to stop Roundup lawsuits - Click Here
Kellogg to split into 3 separate companies - Click Here
Governors form task force to address mass shootings - Click Here
Panel releases video supporting Sherrill's claim - Click Here
Judge: New York's lawsuit against NRA can move forward - Click Here
Police: Capitol tour on January 5, 2021, wasn't suspicious - Click Here
Court rejects Trump-era finding weed killer is safe - Click Here
House OKs security boost for justices and families - Click Here
Group of senators makes deal on gun legislation - Click Here
Don't let your first car be a $30K mistake - Click Here
House approves 'red flag' gun bill, but its fate is dim - Click Here
No, you're not imagining it - package sizes are shrinking - Click Here
Activists say cyber agency weakens voting tech advisory - Click Here
Wray: FBI blocked cyberattack on children's hospital - Click Here
US sees heightened threat of domestic extremism - Click Here
Senator seek broad oversight of crypto - Click Here
Some cancer patients can skip treatment, 2 studies show - Click Here
Proud Boys documentarian to be among January 6 witnesses - Click Here
Warning signs can show potential mass shooter - Click Here
Canada to cap handgun market with a new law - Click Here
Axon halts plans for Taser-equipped drone - Click Here
Biden appeals for tougher gun laws - Click Here
Putin-linked elites, yachts, aircraft and firms targeted for new sanctions - Click Here
Shooting victims testify before Congress - Click Here
Will Congress now act on guns? - Click Here
Senate GOP blocks terrorism bill - Click Here
Gunfire at schools at record high in US, research shows - Click Here
Biden signs new policing order - Click Here
Massacre extends Texas' grim run of shootings - Click Here
Protect unborn but don't help poor - this is valuable life? - Click Here
I'm the mom I an because I chose an abortion at 19 - Click Here
House pases domestic terrorism bill - Click Here
Advertising may be rough for social media - Click Here
Hepatitis cases in US, Canada could be linked to strawberries - Click Here
Biden see change for gun limits - Click Here
Biden seeks to boost solar panel production in the US - Click Here
Meta to reveal how its sites' ads target users - Click Here
House passes gas 'price gouging' bill - Click Here
How to avoid crypto 'rug pulls' - Click Here
Congress seeks to help computer chip industry - Click Here
Internet provider join Biden's discount plan - Click Here
Women's health bill failed in Senate - Click Here
Face-scanner Clearview agrees to limits in court settlement - Click Here
Why Asian women are shut out of leadership at American's top companies - Click Here
Social platforms too slow to pull shooting videos? - Click Here
What does 'community policing' even mean? - Click Here
Kick-start your Online clothing resale gig - Click Here
8 steps to break the credit card debt cycle - Click Here
Court emphasizes preliminary opinion is not the final word - Click Here
Rare leak comes in a case of the highest magnitude - Click Here
Anti-abortion groups look ahead to further moves - Click Here
Highly contagious avian flu kills millions of birds - Click Here
Justices tackle high school prayer case - Click Here
Biden makes lynching a federal hate crime - Click Here
Biden expected to release rule on ghost guns in days - Click Here
Biden rule takes aim at ghost guns - Click Here
Biden suspending 10% ethanol rule - Click Here Not Linked!!
Environmental advisers: Justice40 action needed - Click Here
HUD works to remove barriers to housing - Click Here
The Great Resignation not so great - Click Here
Confirmed - Click Here
Many US urban areas will become rural under new criteria - Click Here
Face scanner Clearview AI aims to branch out beyond police - Click Here
A financial checklist to quit your job - Click Here
Worker bring anxiety, question back to office - Click Here
Senate approves bill making daylight saving time permanent - Click Here
US has done away with time changes before - Click Here
After-school programs need staff - Click Here
Biden's China 'pivot' complicated by Russia - Click Here
House votes to further restrict Russian trade - Click Here
Poll: Americans doubt police reform - Click Here
Amazon's voice assistant Alexa to start seeking doctor help - Click Here
Congress OKs Postal Service overhaul - Click Here
Did Amazon violate laws? Lawmakers ask for probe - Click Here
Biden outlines plan, says it's time to return to normal - Click Here
Cyberattacks accompany Russian assault - Click Here
US ends asylum restrictions for children traveling alone - Click Here
Software automates hiring process - Click Here
Study: Human activity near rivers can worsen drought and flooding - Click Here
Uber is adding fuel fee to bills amid rising gas prices - Click Here
High court narrows reach of law on career criminals owning guns - Click Here
Congress passes Emmett Till bill to make lynching hate crime - Click Here
Supreme Court takes on clash over immigration rule - Click Here
FDA clears first smartphone app to deliver insulin doses - Click Here
Senators: CIA has data stash on Americans - Click Here
No-knick warrants face intense scrutiny - Click Here
Advocates cite chronic fatigue danger - Click Here
Over half of US abortions now done with pills - Click Here
Can marijuana really prevent COVID-19? various federal rules complicate research - Click Here
Gun control groups press Biden over ongoing deaths - Click Here
Proud Boys leader indicted in riot - Click Here
Texas suing Meta over sue of facial recognition - Click Here
Does vaccination status matter to singles? - Click Here
White House releases report bolstering unionization - Click Here
Hard thresholds dropped in new opioid guidance - Click Here
News Corp reports hack; link to China suspected - Click Here
Travel groups want to scrap testing requirements to enter US - Click Here
SAT exam going digital, cutting down test time - Click Here
How to start a one-person business - Click Here
White House scientist apologizes for behavior - Click Here
Have a seat - Click Here - located on route in North Brunswick NJ
EPA: New mail-delivery fleet needs more electric vehicles - Click Here
Senate panel advances step to curb tech giants' power - Click Here
Biden issues 'road map' for infrastructure goals - Click Here
States divided on abortion limits - Click Here
States weigh 'bounties' after abortion ruling - Click Here
Is working remotely an option for good? - Click Here
How to prepare for your Zoom interview - Click Here
How to start a one-person business - Click Here
Would you relocate for $10K? Should you? - Click Here
US to give teenage semi drivers a try - Click Here
High court to hear case of Christian flag in Boston - Click Here
Voting bill facing defeat from within - Click Here
For Oath Keepers and founder, January 6 was weeks in making - Click Here
Oath Keeper leader to remain jailed, judge order - Click Here
Dems pivot to fight for voting bills - Click Here
Rising cost hampering small businesses - Click Here
Biden team regroups after defeat in court - Click Here
New COVID variant no cause for alarm, experts say - Click Here
Artificial intelligence can help us avoid future power outages - Click Here
Get skills, not bills, with an unpaid internship - Click Here
New rules on lead in drinking water on way - Click Here
NSO Group spyware used to hack State employees - Click Here
Debate over adoption as alternative renewed - Click Here
Is your company secretly monitoring your work at home? - Click Here
Nissan investing in electric vehicles - Click Here
FTC and 23 states oppose hospital merger - Click Here
FDA: Merck COVID pill effective - Click Here
NYC aims to be 1st to rein in AI hiring tools - Click Here
Biden seeks balance on immigration - Click Here
Women left workforce; will they ever come back? - Click Here
Disability advocates demand reform - Click Here
DOJ continues court battles for voting rights - HOME
High court unlikely to add Puerto Rico to SSI program - Click Here
Democrats push for paid family leave - Click Here
Dems' social, climate bill passes House - Click Here
Microsoft: Russian-backed hackers targeting cloud services - Click Here
Cyberattacks are concerning to most Americans, poll finds - Click Here
Robots hit the streets as demand for food delivery grows - Click Here
Democrats confident methane fee will stay - Click Here
Data of over 40 million exposed in T-Mobile breach - Click Here
What to know about Indigenous Peoples' Day - Click Here
Justices side with police in excessive force cases - Click Here
FDA OKs first e-cigarette, cites benefit for smokers - Click Here
Apple delays plan to scan iPhones for abuse images - Click Here
Facebook puts development of Instagram for kids on hold - Click Here
How to help our daughters cope with toxic images on Instagram - Click Here
Facebook accused of hiding dangers - Click Here
Fixing Facebook - Click
Facebook failed to rid site of sex trafficking - Click Here
State attorneys general probing Instagram's effect on kids - Click Here
Supreme Court set to hear surveillance case - Click Here
Supreme Court allows evictions to resume - Click Here - to read more!
Fate of citizenship for 'Dreamers' rests with 1 - Click Here
Part-time - and no commitment - Click Here
Patriotism, Freedom - Click Here
Court: 18-year-olds can't be denied handguns - Click Here
Bill to protect judiciary back before Congress - Click Here
Judge orders end to DACA program - Click Here
Return on investments - Click Here
Software hack caused by China, US and allies say - Click Here
Chinese banks promise to step up cryptocurrency ban - Click Here
US gives asylum-seekers waiting in Mexico another shot - Click Here
Reason to celebrate - Click Here Juneteenth National holiday.
Leaders: China brings 'systemic challenges' - Click Here
High Court will not review men-only draft registration law - Click Here
Get serious on cybersecurity - Click Here
Many Americans want to keep teleworking - Click Here
Learning to adapt - Click Here
Biden signs latest anti-hate crime bill - Click Here
Streaming services want to stop password sharing -Click Here
Feds to study social media for conspiracies - Click Here
'Geek Squad' email scam targets seniors - Click Here
House passes sweeping voting rights bill - Click Here
3 things to know if you're new to gig work - Click Here
Monoclonal Miracle? - Click Here
Biden's team vows action against cyberhack as threats to the US persist - Click Here
How to spot fake Online shop sites - Click Here
Aid plan to end 'surprise' bills - Click Here
Who needs to commute? - Click Here
IMPORTANT: Administration must take new DACA applications - Click Here
It's time to secure your home network - Click Here
How to launch a business product and get some sales - Click Here
Google ad costs irks small businesses - Click Here
California court says Uber, Lyft drivers are employees - Click Here
5 industries you might consider for investments - Click Here
Dunkin' Donuts in talks to go private with Arby's owner - Click Here
Safe or Scary? - Click Here
IMPORTANT: US bans TikTok, WeChat from phone app stores - Click Here
Justice Department seeks immediate ban on WeChat downloads in the US - Click Here
LinkedIn looking more like Facebook - Click Here
Steroids confirmed to help virus patients - Click Here
Steps for becoming a work-at-home pro - Click Here
Can you trust your mobile payment app? - Click Here
T-Mobile revels new initiative to help block robocalls - Click Here
Facebook knocks Apple's app-store policies - Click Here
4 experts tips to get hired from home - Click Here
Clair's and Icing Websites Compromised to Steal Payment Data - Click Here
Scammers Use Recycled Extortion Tactics in New Campaign - Click Here
Online Shopping and Cyber security - Click Here
Can't find what you need on Amazon? - Click Here
Governor bobbleehads will support frontline workers - Click Here - store.bobbleheadhall.com
Smoking, Vaping could worsen virus symptoms - Click Here
Supreme Court upholds ban on robocalls - Click Here
Tax/Scams/Consumer Alerts - Click Here to read more information.
Personal Information of 5 million Marriott Customers Breached - Click Here
NJ gun law stands, as high court refuse appeal - Click Here
Public restrooms getting redesign - Click Here
GOP senators crafts bill that would put restrictions on use of chokeholds - Click Here
GOP bill would discourage chokeholds - Click Here
Dems: GOP police bill 'not salvageable,' demand talks - Click Here
Poll: Most want major police reforms - Click Here
Split Congress stalls on police reform plan - Click Here
LGBTQ workers get win in high court - Click Here
Quaker Oats retiring 131-year-old Aunt Jemima brand - Click Here
For grocery delivery, add extra fees to list - Click Here
Hyundia begins developing 'walking car' - Click Here